- Can Imac Get Hacked
- Can My Mac Get Hacked
- Do Macs Get Hacked
- Do Macs Get Hacked Iphone
- Can Mac Computers Get Hacked
Jun 29, 2020 Several examples of viruses that have infected Apple Macintosh computers include the following. Flashback malware - Infected over 600,000 Apple computers in April 2012; designed to steal user's personal information, including account login credentials.; OSX/KitM.A virus - Infected a small number of Apple computers in May 2013; designed to take screenshots of a user's desktop and upload. Can Macs get WannaCry? Put simply, no. WannaCry takes advantage of a bug in Microsoft Windows' network file sharing system, a technology called SMB. Once WannaCry gets onto a single computer on.
Feb 07, 2018 Macs don't get as many viruses as PCs, but users are still vulnerable to phishing and other exploits. And don't buy hacked accounts to porn sites (the ones for sale on the dark net). Sep 20, 2008 Yes Macs can get hacked, it all depends on your network and your password. I did computer tech for ten years, I never had a Mac running MacOs X get a virus, malware or adware. There are over 1,000,000 Windows viruses. Hackers get just enough information to hack into a credit or debit card account to make fraudulent purchases (usually online) where they can get away with it. Hopefully, your bank has systems in place to track suspicious activity. You can do your part by opening up your at-risk accounts and checking your account activity yourself. May 07, 2020 There’s an age-old belief in the tech world that Macs don’t get malware. Well, we know that isn’t true — Mac security firm Intego uncovered several new threats specifically targeted at. Hello my Facebook has been hacked and my password was changed. I can no longer login in to my yahoo mail because I have not used it in years so it got deleted. That means I can’t see the code that is being send. I have no idea what else to do to get my Facebook back. Can you please help me recover it. On Facebook I go by Bravo Jenny.
Back up, wipe, reinstall, migrate in only docs, change all passwords on mail and Wi-Fi and all connected devices.
Don’t discuss trading or financials outside strictly necessary conversations, and don’t expect add-on security software or hardware products to actually do what it claims, and do expect at least some of those products to potentially open up new avenues for exploitation.
Don’t run a guest network. Or if you do need a guest network, isolate it. WPA2 with a long pre-and complex shared key,
Use a password manager.
Safari on recent releases can show shared passwords, with a warning triangle in its password store. (Safari uses Keychain for storage, but the caution marker is something that only Safari shows and nor Keychain.) Remove most or all duplicates, when you’re changing passwords everywhere.
Can Imac Get Hacked
Backups, wipe, reinstall from known-good, change all credentials, enable multi-factor authentication where that’s available.
Backups are a key part of breach recovery.
Notify your financial institutions. Also notify your local police.
Oct 27, 2018 10:00 AM
Signs Your Email Was Hacked
With the advent of #Staysafe and #Shelterinplace, the increase of personal email com-munication has skyrocketed. This increase has allowed clever hackers to worm their way into installing viruses via attachments as well as other common techniques.
You Know You’ve Been Hacked When…
Your Contacts are Receiving Messages Not Sent By You
Messages that seem to come from you to friends or business contacts must alert you to a severe problem on your computer. Friends may have the confidence to let you know about these emails, but business contacts or professional associates may not. Hackers can install malware on their computers through email attachments, and the intruder can find a password with an amazingly small amount of effort.
Your Online Password Stops Working
As a regular visitor to your favorite sites, you know the password that each one requires. While you may accidentally strike a wrong key and create a typo, the chances of doing it twice seem highly unlikely. Since you know that the password appears not to work, you may need to consider the possibility that someone has hacked your email.
Can My Mac Get Hacked
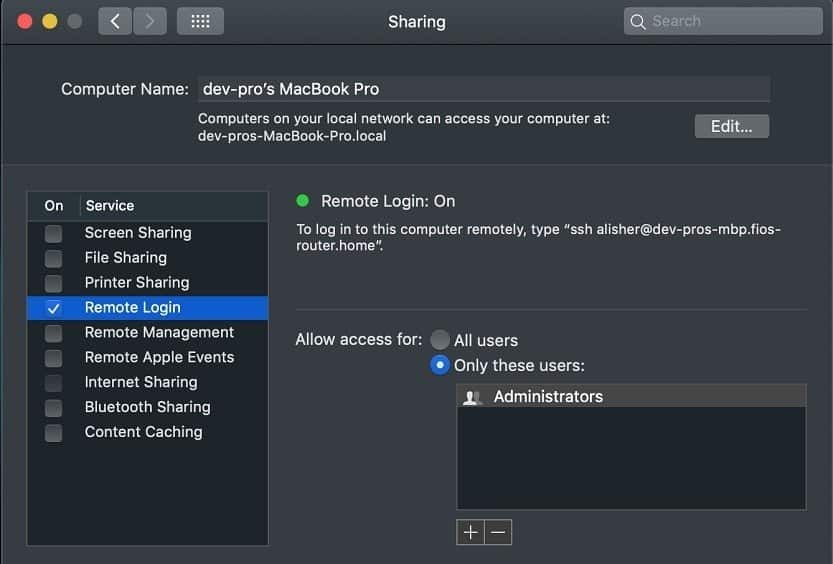
Once inside your computer, hackers have almost a free reign to look for your pass-words. Many people create a list of passwords for convenience, but the benefit to a hacker who finds such a file can reach significant proportions.
Slow and Erratic Computer Performance
Do Macs Get Hacked
Unpredictable conduct by your computer can mean that a virus may have infected it. The sluggishness that replaces the usual prompt response that you expect tells you that you have a problem. Spyware, a malicious type of software, can track your online activity, tamper with your files, and even steal your private information.
When you consider the burden that spyware can place on your system, you can under-stand the reason for its lackluster speed. While you probably did not notice anything wrong when you downloaded a picture from a website or clicked on an attachment in an email, a virus could have accompanied it. Until you remove the virus, you may feel as though you have someone watching you, and you do.
Watching for Ransomware
A particularly insidious form of malicious software comes with an ability to make you pay for the privilege of controlling your computer. Ransomware can enter your system through emails, and you allow it to do so when you click on an attractive attachment from an unknown sender. Ransomware can lock your files and make them inaccessible. The troublemakers who put it there demand a fee to release its grip on your system.
Maybe more dangerous than other malicious invasions of your computer, ransomware carries a penalty that can completely deny you access to your files and cost you money to get it back. As a caution that reminds you of the hazard of opening attachments that can cause damage to your computer and your finances, an email that installs ransom-ware deserves attention immediately.
What Should I Do if My Email is Hacked?
Change your password
This is the first thing you must do to ensure that the hacker can’t get back into your ac-count. Your new password must be complex and unrelated to previous passwords. Al-ways use 8-10 characters with a mix of upper and lower case characters as well as numbers and symbols.
Reach out to your email contacts immediately
A big part of the hacker’s strategy is to ‘get their claws’ into your address book to hook others as well. Send a message to all of your email contacts as soon as possible. Let them know they should avoid opening any emails (most likely loaded with malware) that have come from you.
Change your security question
If you have security questions associated with your email account, be sure to change them too. Make them unpredictable and niche.
Enable Multi-Factor Authentication
Do Macs Get Hacked Iphone
Yes, multi-factor authentication adds another step to your login, but it also adds another layer of protection. Enabling this will mean that in addition to your password, you will need a unique one-time use code to log in. This is usually sent to your mobile phone.
Scan your computer for malware and viruses
This is an essential step. Comprehensive security software will provide you with a digital shield for your online life. McAfee Total Protection lets you protect all your devices – including your smartphone – from viruses and malware. It also contains a password manager to help you remember and generate unique passwords for all your accounts.
/Locked_VictorDeSchwanbergSciencePhotoLibrary-583cdbf83df78c6f6a02fb02.jpg)
Change any other accounts with the same password
This is time-consuming but a worthwhile effort. Ensure that you change any other ac-counts that use the same username and password as your compromised email. Hackers love when we use the same logins for multiple accounts.
Stay protected
Can Mac Computers Get Hacked
While email can pose potential security risks, antivirus software protects your computer system from potential damage. Programs that run efficiently in the background detect and eliminate threats. Awareness and preparedness can help you thwart attempts to hack private information and let you maintain a secure environment online.
댓글